Ransomware and malware are often talked about in the same context, but they have different meanings.
All ransomware is malware, but not all malware is ransomware.
Malware, or malicious software, refers to any type of software created by cybercriminals to gain access to systems or access data. Malware includes everything from computer viruses to keyloggers.
While ransomware is considered a type of malware, it deviates from malware in the way it is used by attackers. Ransomware is designed to block access to files and systems and extort money from victims.
In almost every scenario, a victim of a ransomware attack is asked to pay a fee to their attacker to regain access.
This article will further explore the key ways in which these two types of malicious software differ.
What is ransomware in simple terms?
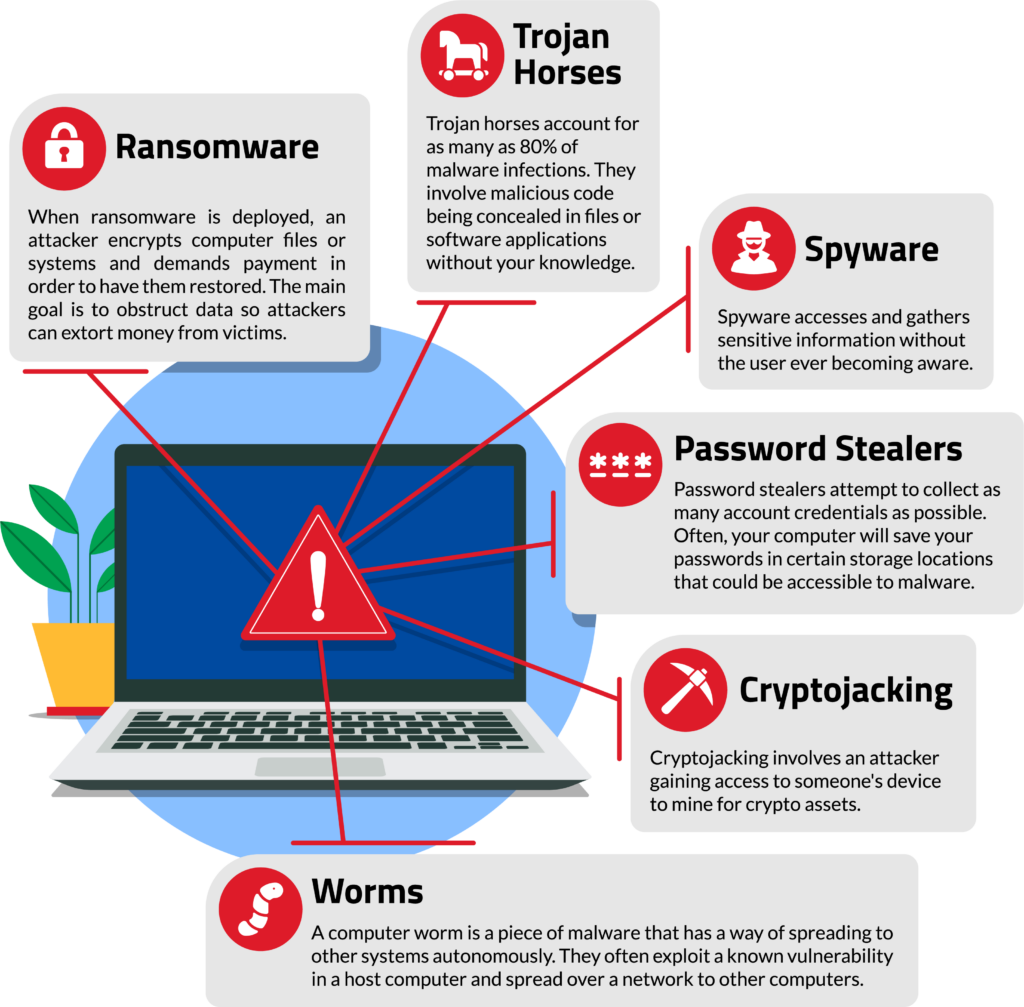
Technically, ransomware is a form of malware. When ransomware is deployed, a victim’s files are encrypted. Sometimes, an entire system is encrypted. To regain access to their assets, a victim is asked to make a payment to the attacker.
As someone who is under attack, you should avoid paying the ransom entirely.
The US government has created restrictions that make it illegal to pay the ransom. There is no way to guarantee that victims aren’t paying a foreign government, a malicious actor, or another entity placed on a banned list.
Additionally, you should not pay the ransom because there is no guarantee your files will be unlocked. Attackers may not give you the information back, and they may still have access to your data and release it elsewhere.
Stages of Ransomware
Generally speaking, ransomware attacks are made up of four stages.
Delivery / Initial Access
There are several ways that ransomware attacks can be initiated. A common approach is for attackers to use phishing tactics. Once a recipient clicks on a link or email attachment, the ransomware threat is delivered.
Although many of us would like to think we could spot a phishing attack fairly easily, the numbers don’t agree.
In the first quarter of 2022, more than 1 million phishing attacks were recorded.
Today, phishing activity is becoming more sophisticated, with social engineering becoming the new normal. These attacks attempt to trick the user with messages purporting to be from trusted contacts or established organizations.
Discovery and Persistence
The discovery stage involves attackers scanning networks to identify additional potential weaknesses or valuable assets in order to elevate their access to the environment.
They may assess networks, servers, users, assets, types of backup systems, and more.
Attackers will take advantage of freely available tools and techniques to expand this access.
Additionally, attackers will seek to install methods of persistence in the environment so they can freely return as needed. This may involve creating backdoors into the environment or stealing legitimate passwords.
Their goal is to add as many persistence methods as possible so they can gain and retain as much access as they can.
Ransomware Delivery / Encryption
Once administrative access to the environment has been achieved, attackers are free to exfiltrate any or all data or encrypt it as they make ransom demands to the victim. Typically, they will push encrypting ransomware to each server and workstation they have gained access to in order to maximize the impact.
Establish Communication
At this point, attackers will reach out to the victim and let them know their information has been compromised. They demand a ransom and encrypt data or threaten to release it online.

What’s next?
If you find that you are the victim of a ransomware attack, there are paths you should take rather than paying the ransom.
Redundant, up-to-date backups of your business information can help restore your data and get you back to work; however, this requires having them to begin with.
Working with a knowledgeable individual or company is also key so you can properly secure your systems and prevent future attacks.
What is malware and why is it harmful?
Malware is an umbrella term that refers to any type of malicious software. Here are several different types of malware other than ransomware.
Trojan Horses
Trojan horse attacks are among the oldest types of malware, with the first example dating back to 1975.
Today, they’re one of the most common types of malware encountered, accounting for as many as 80% of all malware infections.
Trojan horse attacks involve malicious code being concealed in files or software applications that, on the surface, look completely inconspicuous.
In reality, attackers gain access to your computer or data and can use it to perform malicious actions.
Spyware
Spyware is also a constant threat.
This type of malware is designed to access and gather sensitive information, without the user ever becoming aware.
Adware also falls into the malware category. In simple terms, it’s the software that allows banner ads to be displayed across web pages as users surf the internet.
Password Stealers
Password stealers are commonly employed by attackers in an attempt to collect as many account credentials as possible once installed on a computer.
Many times, your computer will save passwords in certain storage locations (such as Chrome stored passwords, the Windows Credential Manager, or the macOS keychain) that could be accessible to malware.
Stealing your passwords provides an attacker with many additional opportunities such as logging into your accounts.
Cryptojacking
Cryptojacking is a fairly new addition to the malware family.
When we talk about cryptojacking, we’re not talking about an attacker stealing someone’s crypto assets (which can be an issue through other forms of malware such as password stealers).
Rather, cryptojacking involves an attacker gaining access to someone’s device to mine for crypto assets.
Many types of systems can fall victim to this kind of malware attack, including cloud infrastructure, servers, and everyday desktop computers.
Worms
A computer worm is a piece of malware that has a way of spreading to other systems autonomously.
Worms often exploit a known vulnerability in a host computer and spread over a network to other computers.
Usually, worms negatively impact networks as they continue to spread and infect more systems.
In 2004, the Mydoom attack cost the equivalent of $52 billion in damages in today’s money.
How do ransomware and malware attacks differ?
Although there’s a substantial overlap between ransomware and malware, you can identify which one you’re dealing with by assessing a few key factors.
The main difference between ransomware and malware attacks is the way they are monetized.
With ransomware, attackers encrypt your data and demand payment in order to have it restored. The main goal is to obstruct data so attackers can extort money from victims.
Attackers will also make it explicitly clear that your system has been compromised.
With other forms of malware, attackers don’t demand payment or obstruct your data.
Their goal is to hide on your computer, run commands without you knowing, and steal information.
You may never know if malware has infected your system—attackers will just continue taking data and using your computer for malicious purposes.
How do you remove ransomware and malware?
We recommend working with a trusted individual or cyber security company to remove ransomware or malware from your computer.
If you attempt to remove malware or ransomware yourself, you could open yourself up to additional risks or potentially cause irreversible damage to your data in a recovery situation.
In addition, there is no guarantee that you can remove all persistence methods yourself. The attacker may have other ways to access your system. Failing to remove all persistence methods could leave you vulnerable to potential attacks in the future.
Finally, additional accounts may be affected as a result of passwords being stolen from your system. The attackers may have gained passwords to your other accounts and could compromise those as well.
The entire scope of the incident needs to be taken into consideration and all accounts need to be adequately protected.
If you aren’t careful, this might not be one isolated incident and could instead lead to a series of attacks.
How can I prevent ransomware attacks?
Having a robust backup strategy for your personal and business accounts is absolutely essential to protect against ransomware and other forms of malware.
In the worst possible scenario, you’ll at least be able to recover your data and return to work and other daily activities after recovery efforts.
Prevention is key.
How to protect against ransomware and malware
Although ransomware is a fairly new type of cyber security threat, there are several steps you can take to prevent a ransomware attack and restore your data properly.
Online and Offline Backups
Firstly, make sure you’re regularly backing up a complete set of your data and have a recovery plan in place that takes overall recovery time into consideration.
Ideally, you should be storing your data in at least three secure locations, with one of these being offline.
Minimize Attack Surface
Eliminate needless systems or accounts to help prevent attacks.
Your business shouldn’t have outdated legacy systems, and it’s important to limit available attack surfaces whenever possible. The more systems or software you have to maintain, the more opportunities attackers will have to compromise them.
When it comes to your personal life, be mindful of the accounts you create and the data you share openly.
Maintain a small digital footprint when possible and monitor your accounts frequently.
Keep Software Patched and Updated
Your software and systems should be updated regularly to avoid new vulnerabilities that are discovered.
Most antivirus software and web browsers will stay up-to-date automatically. However, some applications may require manual intervention to apply patches or updates.
Never ignore updates as these provide you with important security protections regularly.
Don’t Reuse Passwords
Never reuse passwords for different accounts. If one of your accounts is compromised and you used the same password for another system, that account is at risk as well.
Password managers can help with allowing you to create unique, strong passwords for each account you have.
Cyber Security Awareness
To combat phishing emails and malware attacks, educating your teams on email best practices is essential.
At the top of the list, make sure your teams know not to open messages from unknown senders. If a message from a new recipient has to be accessed, approach internal links and attached files with caution.
Email client apps should also be updated regularly. For cybercriminals, legacy systems and out-of-date client apps are easy pickings.
Finally, make sure cyber security awareness is at the heart of your workplace culture.
When it comes to awareness training, hammer out the fundamentals of safer web surfing.
Create strong, unique passwords or passphrases.
Ultimately, you’ll want to limit user access privileges and employ multi-factor authentication whenever possible.
Final Thoughts
Ransomware and malware share many common elements, and you can often apply the same techniques to safeguard yourself against attacks.
Protect yourself against malware with reliable antivirus software, modern cyber security awareness, and data backups.
With ransomware, attackers can quickly monetize your data through encryption and extortion. A strong backup strategy is essential to defend against the risks associated with ransomware.
Make sure you’re at the top of your game when it comes to cyber security awareness, network segmentation, and data backup & secure storage.


